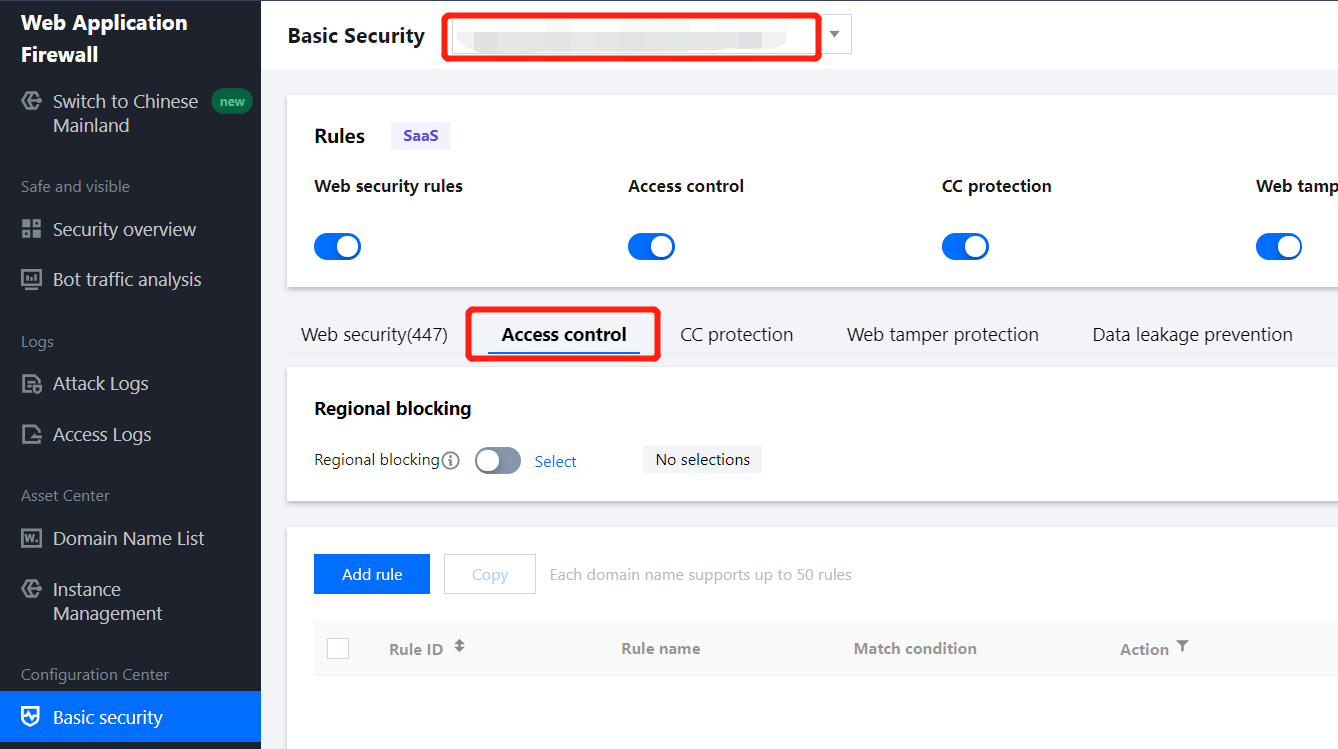
Configuring a Geolocation Access Control Rule_Web Application Firewall_User Guide_Rule Configuration_Huawei Cloud
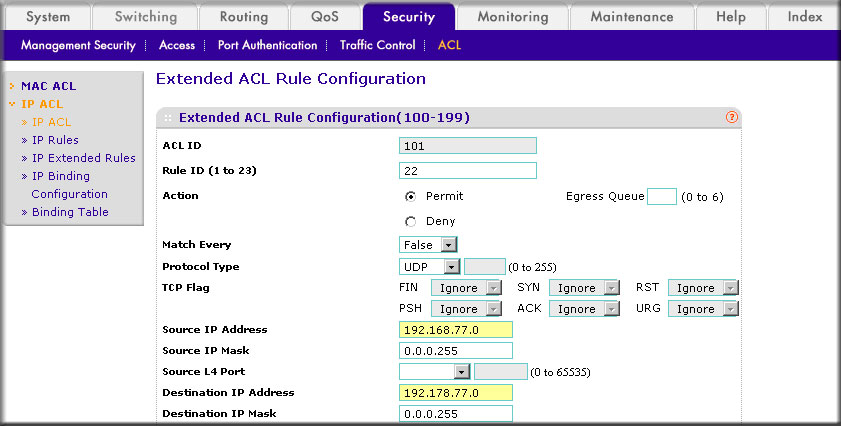
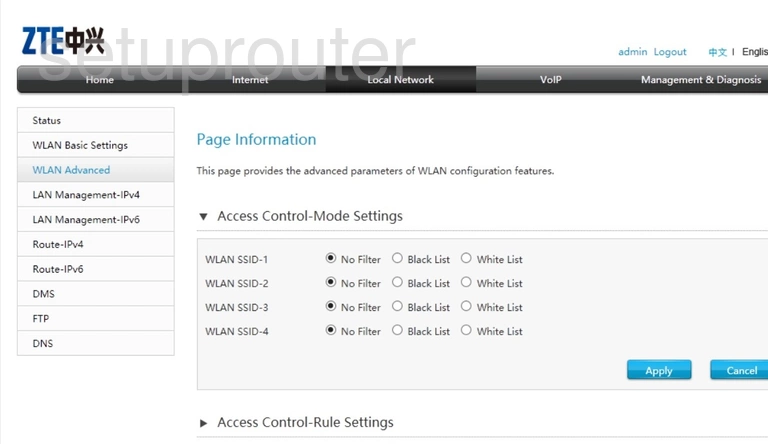
How do I set up an IP Access Control List (ACL) with two rules using the web interface on my managed switch? | Answer | NETGEAR Support
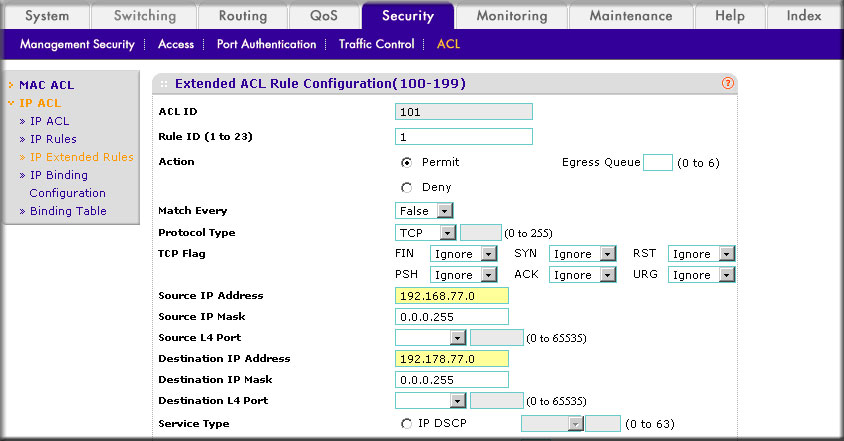
How do I set up an IP Access Control List (ACL) with two rules using the web interface on my managed switch? | Answer | NETGEAR Support







![PDF] A Survey on Administrative Policies in Rule-Based Access Control | Semantic Scholar PDF] A Survey on Administrative Policies in Rule-Based Access Control | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a4a3d0c213a19458a07ea631e4135dd520a4fe48/3-Figure2.3-1.png)

.jpg)